Anonymous Communication
Overlay Communication
- 核心思想
- Handle routing at the application layer
- Tunnel messages inside other messages
威胁模型 Threat Model - Insider Byzantine Attacker
With limited view of network: an attacker might have tight control over a network.
- 攻击手段
- Traceforward Attack - passive attacker
- traces messages from sender, thwarts receiver anonymity
- Marking Attack - active attacker
- marks messages and discovers markded msg elsewhere
- Traceforward Attack - passive attacker
Anonymizing Proxy
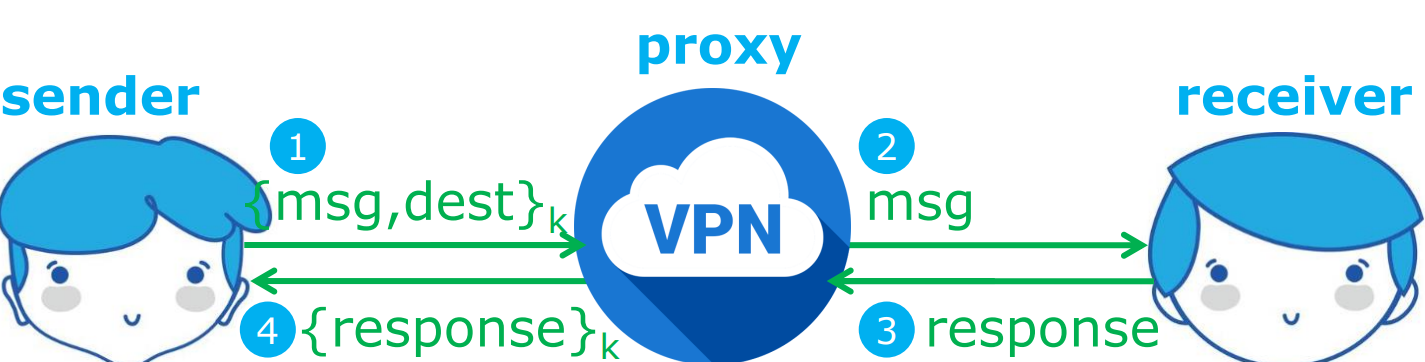
- 核心思想
- 在 sender 和 receiver 之间加入第三方
- sender 和 proxy 之间对 内容 和 目标地址 进行加密
- 安全性
- 如果攻击者在 sender 和 proxy 之间,receiver 是保密的
- 如果攻击者在 proxy 和 receiver 之间,sender 是保密的
- 但是如果有两个攻击者在两端合作,则不具有保密性;或者攻击者是 proxy 自身,也不具有保密性
- 优点
- 设置简单
- 接收方不需要参与加密过程
- 在网络中被普遍使用
- 缺点
- 需要可信任的代理(第三方)
- 保密性依赖于攻击者的位置
- 如何避免攻击者窃听? - Crowds Algorithm
- 如何保证代理是可信的? - Source Routing
Crowds Algorithm
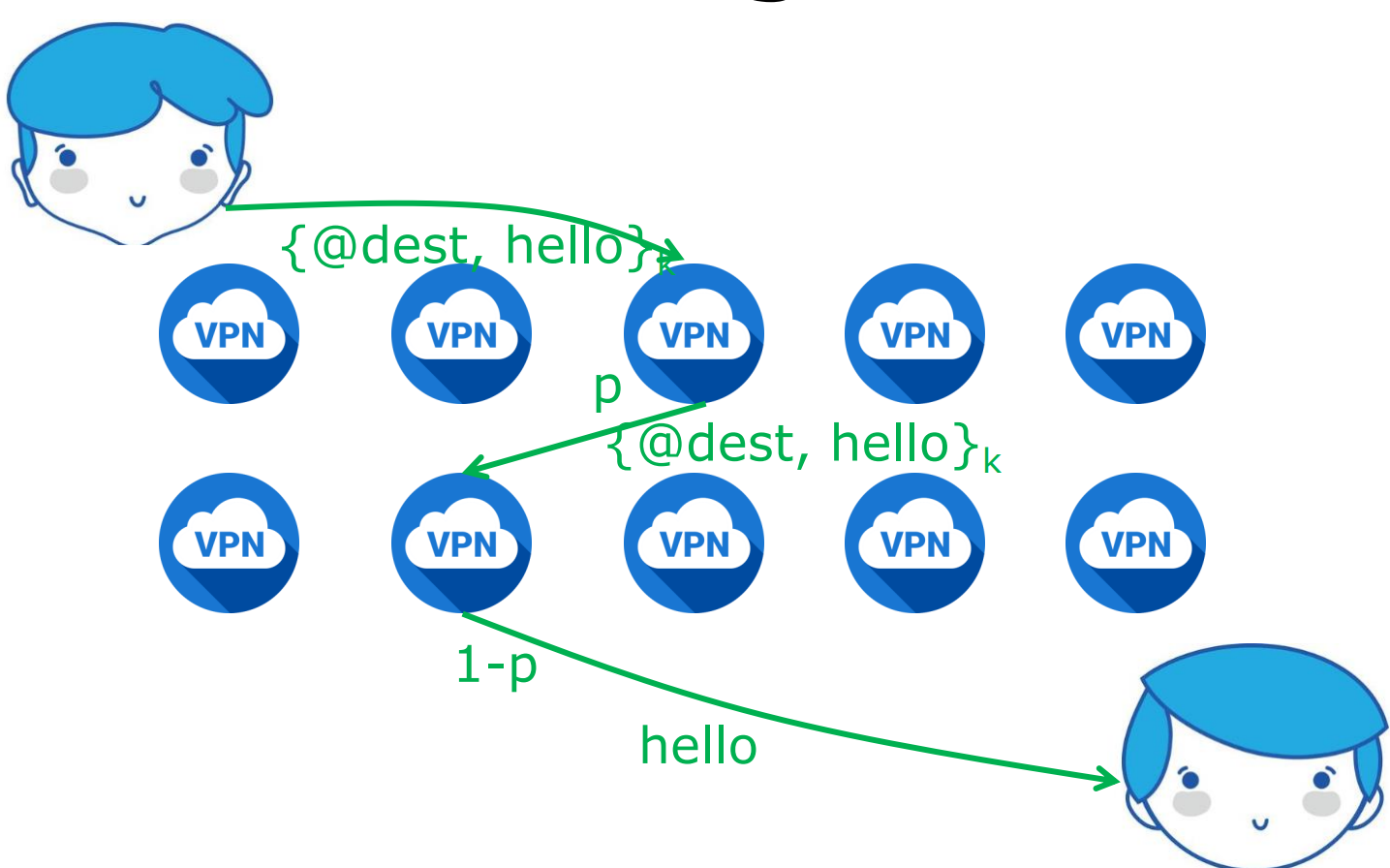
- 核心思想
- 使用人海战术,让信息在众多路由器中传播
- 其中的每个节点都被称为 Jondo
- 算法
- 将信息传递给随机一个 Jondo
- 有 p 概率,信息被传给另一个 Jondo
- 有 1-p 概率,信息被传递到目标地址
- 缺点
- 必须信任所有的 Jondos
Source Routing
- 核心思想
- 允许发送者指定传送路线上的 Routers
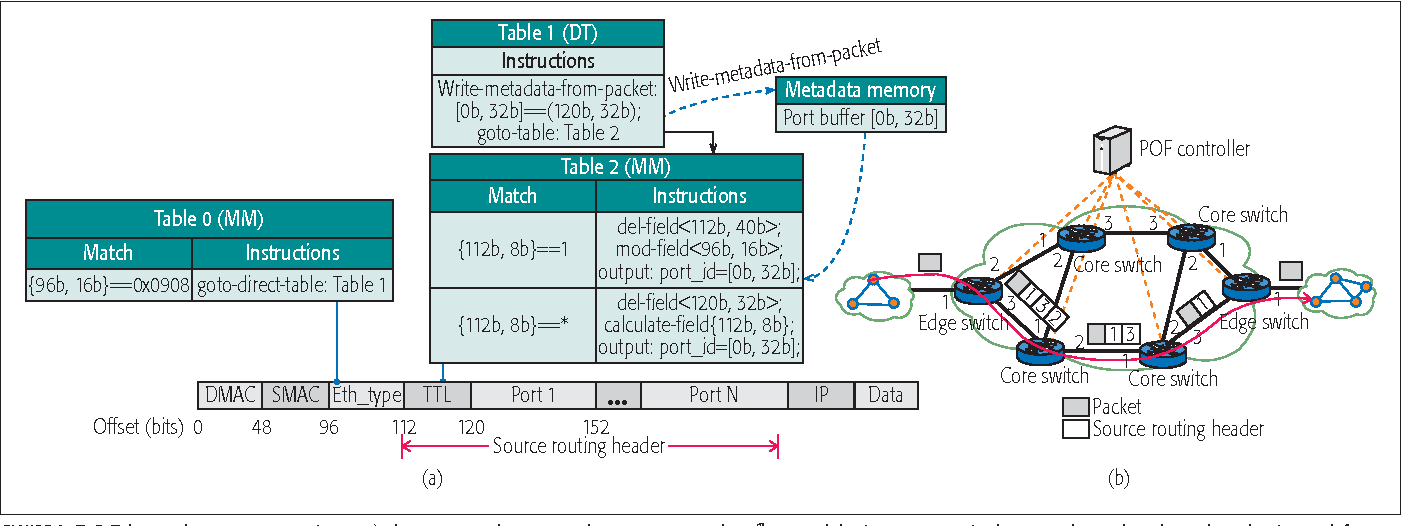
POF-based Source Routing
- Protocol Oblivious Forwarding 协议无关转发机制
- 使用 forwarding table 指定每次路由转发的端口号
- 为了防止端口号泄露,需要对非邻居隐藏自己的端口号
Onion Routing
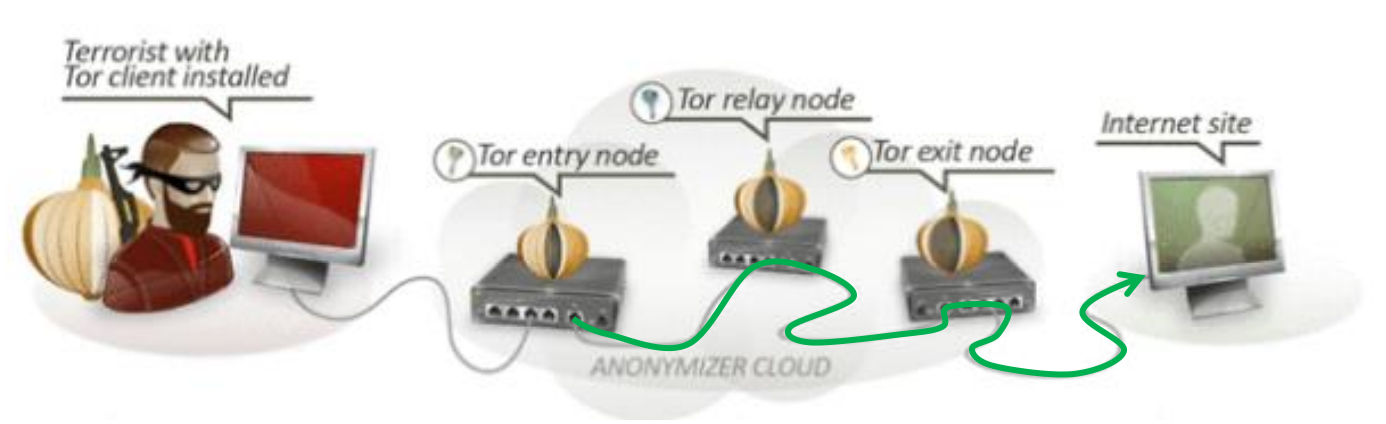
- source-routing based anonymous overlay communication
- 运行机制
- 访问 Tor entry,随机选择一系列的 Tor 路由并构成一条传输路径
- 从 directory node 获取一个公钥,与第一个节点 A 协商密钥;第一个节点与第二个节点协商密钥,以此类推,直到建立起整条链。
- 将数据包
通过这条路径进行传输 - 维护在源和目的地之间的双向持久的多跳路径,以保证回复的数据包能够沿着传输路径返回
- 加密机制
- Layered Encryption:Tor 路由将对数据包进行层层加密
- Leaked routing info:只有前后两个节点知道彼此
Darknet
Portions of the Internet purposefully not open to public view or hidden networks whose architecture is superimposed on that of Internet.
Attacks
- Tor Traffic Correlation
- Passive monitoring
- Active attraction
- 部署一个 Tor 路由
- 吸引 Tor 流量
- 对流量进行分析和关联
- Path Selection Attack
- 攻击原理:利用 Tor path selection algorithm:根据节点带宽进行加权概率分布选择下一个节点。将当前中继 relay 设置成高带宽,以增大被选中的概率。
- 如果控制了第一跳,则能够识别发送者;
- 如果控制了最后一跳,则能够识别接收者。
- Counting Attack
- 攻击原理:利用数据包的编号总是递增的这一原理,通过计数数据包的编号以关联流量。
- Low Latency Attack
- 攻击原理:Tor 路由对每个链路分配队列,根据轮询决定出队顺序。通过不断地向目标路由发送数据包,检测延迟以推断与目标路由的连接的节点的活动状态。
- Cross Site Attack
- 攻击原理:部署 Tor 路由,访问暗网并爬取交易信息,从中提取比特币账户并在公网上进行查找。